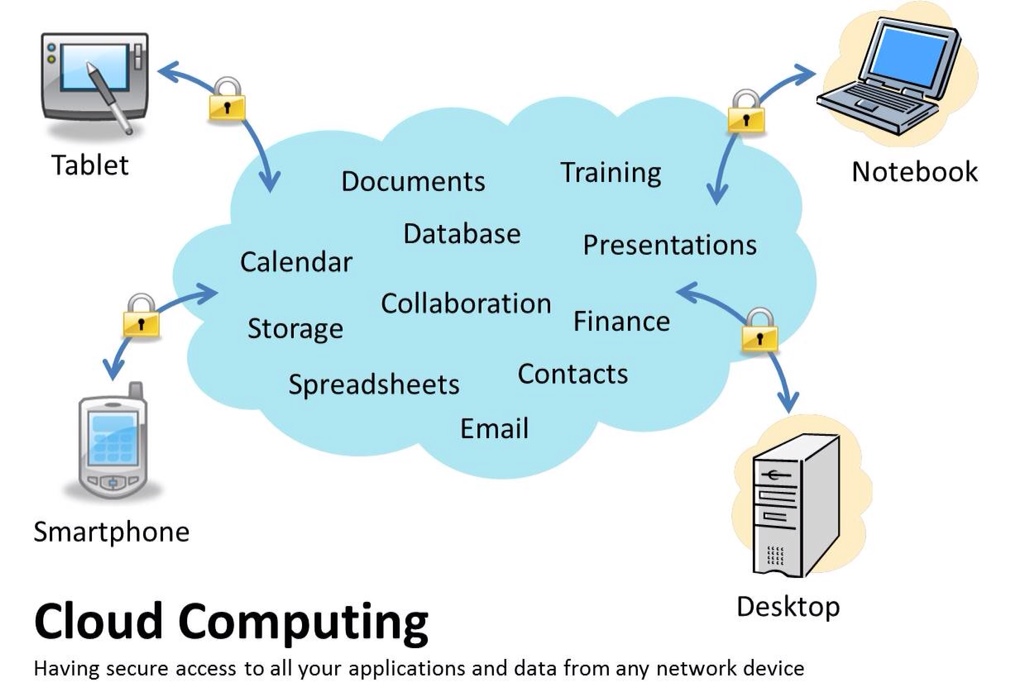
The information housed on the cloud is often seen as valuable to individuals with malicious intent. There is a lot of personal information and potentially secure data that people store on their computers, and this information is now being transferred to the cloud. This makes it critical for you to understand the security measures that your cloud provider has in place, and it is equally important to take personal precautions to secure your data.
The first thing you must look into is the security measures that your cloud provider already has in place. These vary from provider to provider and among the various types of clouds. What encryption methods do the providers have in place? What methods of protection do they have in place for the actual hardware that your data will be stored on? Will they have backups of my data? Do they have firewalls set up? If you have a community cloud, what barriers are in place to keep your information separate from other companies? Many cloud providers have standard terms and conditions that may answer these questions, but the home user will probably have little negotiation room in their cloud contract. A small business user may have slightly more room to discuss the terms of their contract with the provider and will be able to ask these questions during that time. There are many questions that you can ask, but it is important to choose a cloud provider that considers the security of your data as a major concern.
No matter how careful you are with your personal data, by subscribing to the cloud you will be giving up some control to an external source. This distance between you and the physical location of your data creates a barrier. It may also create more space for a third party to access your information. However, to take advantage of the benefits of the cloud, you will have to knowingly give up direct control of your data. On the converse, keep in mind that most cloud providers will have a great deal of knowledge on how to keep your data safe. A provider likely has more resources and expertise than the average user to secure their computers and networks.